Ringus, established in 2008, is a spin-off subsidiary of a financial listed company and become an IT consultancy and support provider with a vision to deliver solutions that optimize business operations and digital capabilities. With our presence in Hong Kong, Australia, United Kingdom, Macau and Taiwan, our stretch reached across the globe.


Young & Energetic
Eager to drive for business success with innovative mind in practical solution

Professional & Intelligent
Our capabilities is demonstrated with solid experience, successful case and relevant qualification
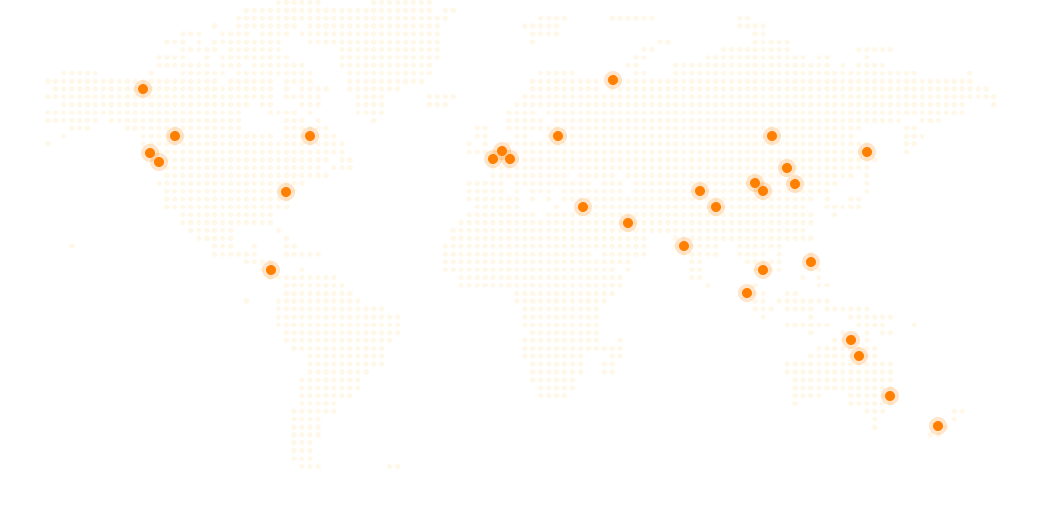
With Presence
- Hong Kong
- Sydney
- Taiwan
- London
- Macau
Asia Pacific
- Cambodia
- Dubai
- India
- Jordon
- Loas
- Malaysia
- New Zealand
- Singapore
- Thailand
- Tokyo
- Vietnam
China
- Beijing
- Chengdu
- Guangzhou
- Shanghai
- Shantou
- Shenzhen
North America
- Mexico
- Miami
- New York
- Panama City
- Phoenix
- San Francisco
Europe
- Denmark
- Germany
- Netherland
- Poland
Our Stretch and Edge
There are more than 30 cities accross the globe with Ringus's footprint. With our centralized hub in five locations, We have built a strong team that delivering our professional service to our clients and achieve success together.
Our talent pool comes from various of professional background In across different service teams, including professional security / privacy service, digital solution service, Outsystems digital transformations and financial technology service team. Our project working workgroup collaborates as to maximize the value to our clients.









